Hacking the SEC: How Passwordless Security and 3rd Party Due Diligence Can Mean the Difference Between Safety and Scrutiny
In its Global Risks Report 2023, The World Economic Forum includes “widespread cybercrime and cyber insecurity” in its list of the top 10 risks that “are converging to shape a unique, uncertain and turbulent decade to come.” It drills down further in an article on its 2023 annual meeting, noting, “Hackers are increasingly targeting IT and physical supply chains, launching mass cyberattacks, and finding new ways to extort businesses, large and small.”
Today, no organization is immune from the risk of being hacked. The Duke University/CFO Magazine Global Business Outlook has reported that “more than 80 percent of U.S. companies indicate their systems have been successfully hacked in an attempt to steal, change or make public important data.”
On January 9, the Security and Exchange Commission (SEC), which is responsible for overseeing more than $100 trillion in securities trading on U.S. equity markets annually, had its official account on X (formerly Twitter) taken over. The hacker posted a message announcing that the SEC had approved an exchange-traded fund (ETF) for bitcoin. According to Coindesk, which covers the cryptocurrency industry, in the 15 minutes before the SEC denied the post, the price of bitcoin jumped 2.5% to $47,500, and dropped 6% to $45,100 after the denial.
On January 12, the SEC released a statement. “While SEC staff is still assessing the scope of the incident, there is currently no evidence that the unauthorized party gained access to SEC systems, data, devices, or other social media accounts.” While this makes the SEC far luckier than most organizations targeted by hackers, the way the account takeover occurred is too common a tale: a SIM-swap attack using a compromised phone number.
An investigation by the agency and its telecom provider determined that the hacker gained control of the SEC mobile phone number associated with the X account, got the telecom carrier to change the SIM for the account, and, once this had been accomplished, reset the X password. Its statement on the investigation also noted that multi-factor authentication (MFA) had been disabled since July 2023 due to issues accessing the account.
The role of telecom providers in SIM-swapping
SIM-swap attacks are up 400% in the last year, with much of the increase coming from organized criminal groups. According to an indictment issued by the U.S. Department of Justice against three individuals who have been charged with stealing $400 million from a single cryptocurrency company, “A SIM swap attack refers to the process of fraudulently inducing a carrier to reassign a cell phone number from the legitimate subscriber or user’s SIM card to a SIM card controlled by a criminal actor.”
The critical point in the success or failure of a SIM-swap attack is the telecom carrier or provider. In a February press release entitled “FCC Must Increase Accountability in Fight to End SIM Swap and Port-Out Fraud,” the National Consumer Law Center (NCLC) noted, “Hundreds of customer complaints to the FCC and the Federal Trade Commission (FTC) each year show that despite victims’ best efforts, SIM swaps are generally successful because provider employees do not know how to address SIM swap fraud, providers refuse to provide documentation of attacks, and provider employees are often involved in the fraud themselves.“
A criminal armed with personal information stolen in a data breach or purchased from the dark web can convince employees of the telecom provider that they are a legitimate customer whose phone was lost or stolen or whose original SIM card was damaged. Or, as the NCLC reported, a telecom employee might also be actively working to help the criminal. A March press release from the U.S. District Attorney’s office in New Jersey reported, “A former manager of a telecommunications company from Burlington County, New Jersey, admitted swapping the Subscriber Identity Module (SIM) numbers of cell phone customers into mobile devices controlled by another individual, who was paying the former manager for the unauthorized swaps.”
Once the SIM card has been changed, the fraudster has access to all the information contained on the phone, from personal banking, credit card, and healthcare accounts to business-related social media platforms and account access processes like identity authentication. As with the SEC incident, they can change the password on any of these accounts, which leaves the legitimate customer unable to access them as the criminal steals information and money or uses the accounts for their own purposes. They can also use the access to the phone itself to circumvent MFA processes that use an authentication app or send a one-time code to the phone as a secondary means of verifying that the person attempting to access the account is the legitimate customer.
In December 2023, the Federal Communications Commission (FCC) issued an enforcement advisory to remind telecom providers of their duty to protect the confidential information of customers that was established in the Communications Act of 1934. New FCC rules that take effect in July are designed to help telecom providers increase customer security and reduce SIM-swaps. These updates include strong customer authentication requirements for all SIM-swapping processes, the need to provide timely notification to customers of changes to their accounts using appropriate channels, safeguards on employee access to customer information, the need to provide clear customer fraud reporting and remediation processes, and mandatory tracking of the effectiveness of SIM-swap protection efforts.
One of the strongest measures both a telecom provider and its customer can take to avoid account takeovers through SIM-swapping is to stop relying on passwords alone for security and account access.
Reducing risks with passwordless security
Two of the biggest issues with passwords include: they are easy to hack or steal; there’s no way to confirm that the person entering the password is the legitimate customer. Even using MFA via an authenticator (app) or an OTP (one-time password) only confirms that the person entering the password has control of the registered device.
Moving to biometric authentication, which uses physical and/or behavioral factors such as a fingerprint, gait, a facial scan, or keystroke analysis, offers much stronger security than passwords do. Because these characteristics are unique to the individual who established the account and are nearly impossible to hack, lose, forget, or duplicate, they can only be used by the account owner and are impervious to ATOs (account takeovers).
As part of the process of opening an account, a customer is asked to provide a facial scan, fingerprint, voice print, or other (perhaps behavioral) factor. A mathematical representation of the user’s factor is created from their input – a template that contains just enough information to verify the customer’s identity when they attempt to access the account. Even if a template is somehow accessed by a fraudster or even stolen, it can’t be used to establish identity, since the live fingerprint or face of the user must also be present. Biometric templates are immune to reverse-engineering.
If biometric authentication is in place, a customer reporting a lost phone and requesting to have the SIM moved to a new device, for example, could be asked by an agent or prompted in-app to provide a fingerprint or take a selfie of their face. If these factors don’t match the fingerprint or facial scan that was provided when the account was initially opened (during identity verification), the request could be denied and the legitimate customer notified of the attempt.
Even if a SIM-swap is successful, users and businesses who have switched to using biometric security to access the information and accounts on a smartphone can limit the damage caused by this form of fraud. For example, a bank account that requires a biometric factor to open (like scanning your fingerprint) is much more difficult for a criminal to steal from than one that’s secured with only a password.
Biometrics increases security without making account access harder for customers or employees. This is a critical benefit, especially since difficulty in accessing accounts gives customers a reason to switch telecom companies in a post-pandemic environment where customer loyalty to their providers is already down 22%. If UX is cumbersome due to traditional security methods (like passwords or OTPs), it can lead users to reduce the security on accounts they access through the phone – exactly like the SEC incident, where MFA had been turned off due to issues the phone owner was having when attempting to access the X account.
Biometrics is an important element in passkey technology, a digital, cryptographic, multi-device credential that replaces passwords. Passkeys are tied to users through elements including biometrics, behavioral and login patterns, and device location, making it hard for a criminal in a different geographic area to impersonate the legitimate customer. Contrarily (and beneficially), passkeys make it easy for legitimate users to securely register multiple devices and accounts.
A customer with a new device, for example, can authenticate with their OS (Operating System) vendor, download the cryptographic keys onto the device, and use those keys to authenticate themselves. A criminal attempting to compromise the device won’t have access to the passkey credentials they need to authenticate with the OS.
Passkeys provide an identity continuum across time and devices that provides protection against single incident criminal attacks, such as a SIM-swap.
Take the first step into the passwordless future
Adopting biometric authentication now, either as the primary source of identity verification or as a more secure secondary factor in an MFA process, can give telecom providers an advantage as they seek to conform to the incoming FCC rules. Using biometric factors to unlock apps and access data on their phones can also help businesses and customers alike increase the security of those accounts and decrease the possibility of account takeovers.
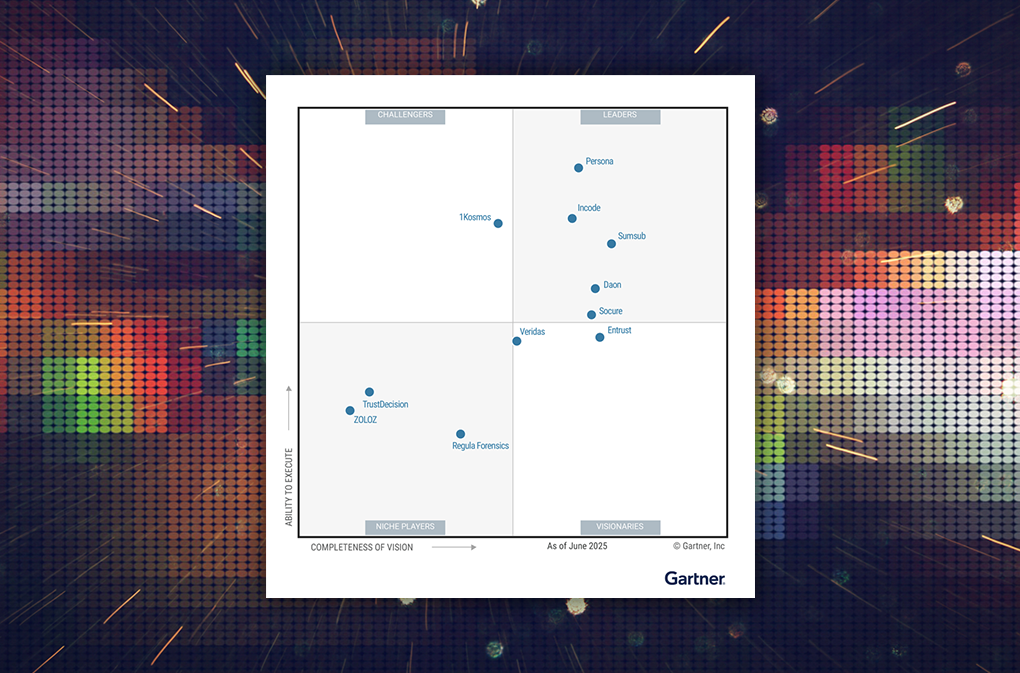
Daon offers a complete portfolio of biometric authentication solutions to help telecom providers and businesses across industries better protect their customers, their data, and their employees.